We’re getting closer to the real fun where we can start provisioning Application access and Securing traffic with Zscaler. Before we can do that we have some work to do.
Let’s connect an Identity Provider (IdP) to our Zscaler Tenant.
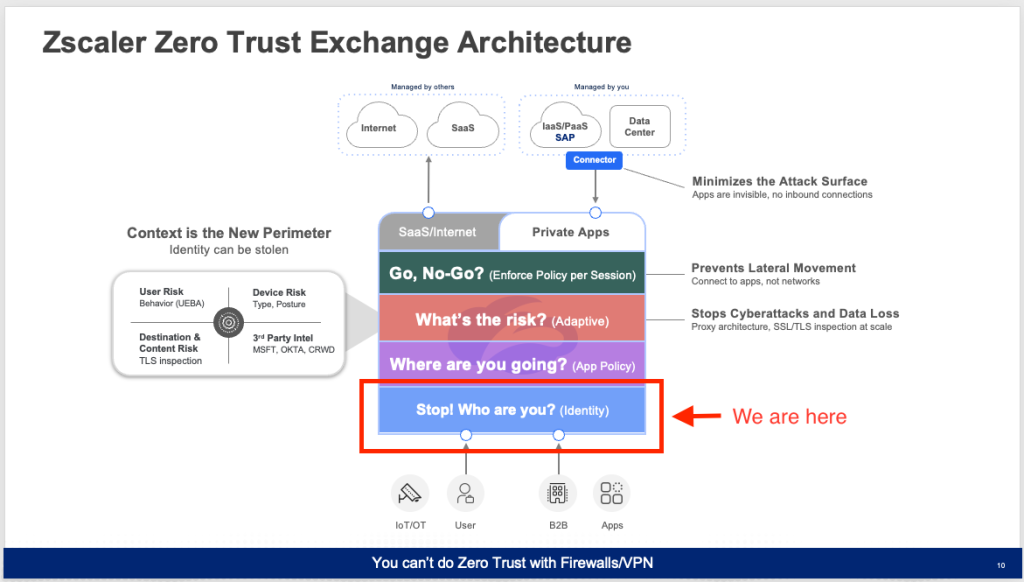
If you’ve seen a Zscaler presentation at all , you’ve probably seen the above image. This effectively maps out the Zero Trust process for Authentication and where it fits in the overall scheme of establishing connections. I’ve highlighted the piece covered in this post in the slide above. See the official documentation here. https://help.zscaler.com/zia/adding-identity-providers
Step 1: Login to your Zscaler Admin Portal for the Cloud your tenant is provisioned on. Assuming you are a customer , partner, or working with your Zscaler team on setting up a PoV test, use the link provided to you.

On the Admin page, go to Administration> Authentication

Then on the “Identity Providers” tab, we’ll select the “+ Add IdP” , if you already happen to have one setup, and are prompted with another option, just select “Add another…” and Next.


On the Add IdP page we’ll need some of the info we saved from Azure before, if you didn’t save it you’ll need to go back into your Azure Tenant and get it.

Enter the following required details:
- Name: Azure (or whatever you want)
- Status: Enabled
- SAML Portal URL:
<Paste in Login URL link you saved.> - Login Name Attribute: NameID <– This is case-sensitive.
- IdP SAML Certificate: Upload .pem file you saved from before
- Vendor: Microsoft Azure Active Directory
You should end up with an IdP profile that looks something like the following.


Now that we’ve connected our Azure IdP, we need to set Zscaler to use it. Navigate back to Administration>Authentication , then just select the SAML Authentication Type. Select Save at the bottom of the page, then be sure to “Activate” your changes.


That’s really it for enabling an authentication source. Next Post I’ll cover off enabling SCIM for updates and changes.